1. What is search parameter injection?
Search parameter injection attacks are a new, sophisticated method used by criminals to obtain your data or even gain access to your PC.
Criminals place adverts on Google that are displayed whenever someone searches for the word “support” and a specific company, such as “support Netflix.” The advert appears directly above the first search hit and is designed to look as if it comes from Netflix itself.
Anyone who clicks on this advert is — and this is the special thing about this scam — not directed to a fake website, but to the original Netflix support website. However, the attackers have entered their own telephone number in the search function on the support page (see image).
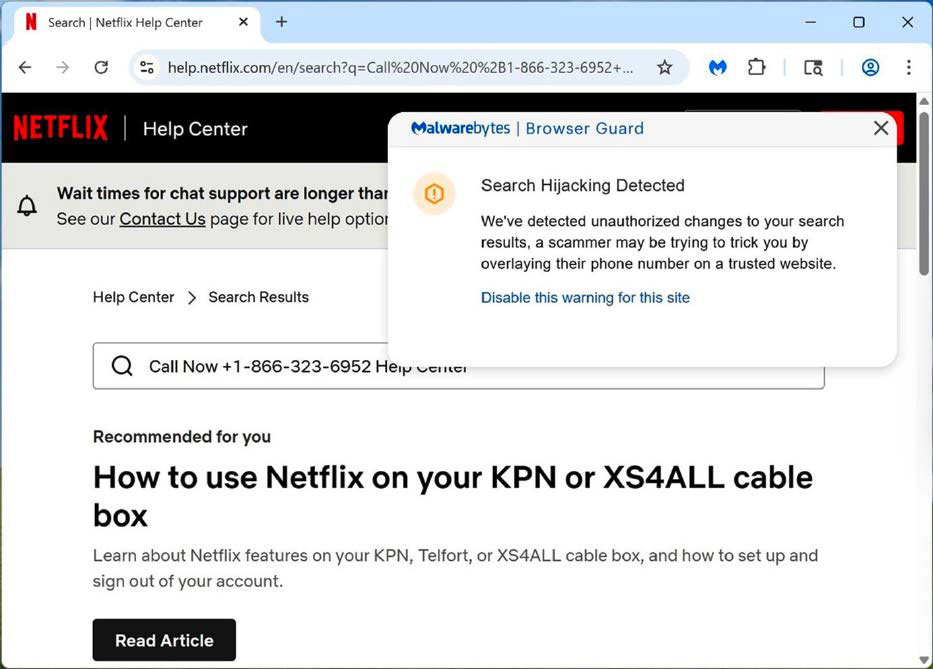
Here, criminals have inserted their own telephone number on the real Netflix support website. Anyone who calls there reveals their data and, in the worst case, risks catching a Trojan.
Foundry
A victim who calls this number then reveals their data to the criminals, such as the password for the Netflix login. In some cases, victims are also persuaded to install what appears to be support software.
However, this is actually a Trojan that gives the attackers access to the PC.
Not only Netflix is affected by this scam; the websites of other large companies such as HP, Dell, and others are also hijacked by the criminals.
How to protect yourself: Many security suites offer a web filter for the browser. This should recognize such attacks. The current malware campaign was discovered by the antivirus specialist Malwarebytes. The Malwarebytes website filter should therefore reliably block these attacks.
2. Is Defender enough?
The Microsoft Defender antivirus program is integrated into Windows as standard. It is free to use, it updates itself automatically, and the integration with Windows could not be closer — after all, the tool comes from the Windows manufacturer itself.
In addition, Microsoft Defender’s virus detection has almost always performed very well in past tests. Defender is therefore sufficient for any IT-interested user who has a healthy level of mistrust towards emails and websites.
However, anyone who is not at all interested in IT security and has never heard of phishing emails and dangerous websites is better advised to use a comprehensive antivirus suite, as this offers more additional protection functions.
Further reading: Best antivirus software for Windows
3. Are passkeys really more secure?
Passkeys are the new superstars when it comes to secure login to online services. Instead of authenticating yourself with a password, you use a passkey.
This is stored on a compatible device (any current smartphone or computer) and released using fingerprint, face scan, or PIN authentication (Windows Hello). As there is no password when logging in with a passkey, it cannot be stolen. Passkeys also provide very good protection against phishing attacks.
So: Yes, passkeys are much more secure than passwords. Wherever possible, you should use passkeys to log in to a service.
However, if you lose your smartphone, you will also lose your passkey. In such a case, it is difficult for an online service to reliably identify a user. In other words, to grant them access to their account again. That’s why there are only a few services that allow you to authenticate yourself using a passkey only. There is still a password for logging in.
One exception is the Microsoft account, which can be used without a password as of this year. In addition, the use of passkeys is not as straightforward as many people think. There are problems, for example, if you have saved passkeys both in the operating system (such as Android) and in a password manager.
4. How do I protect myself from crypto miners?
Crypto miners are malware that use your PC to calculate digital money. The threat comes in two forms:
- First, as classic malware that embeds itself in your computer. You can block this malware with good antivirus software.
- Second, crypto-miners lurk on the web: Javascript-based mining is embedded on prepared websites, which becomes active directly when the page is called up. In this case, the malware only runs while the browser session is open and disappears when the page is closed.
How to protect yourself: To prevent mining in the browser, use the Opera browser for unknown and possibly infected websites. It automatically blocks mining code.
5. How dangerous are AI attacks?
Artificial intelligence creates convincing texts, cloned voices, fake videos, and functional program code within minutes. It finds security loopholes in software and server services and is extremely inexpensive. Cyber criminals also take advantage of this.
However, the question of how dangerous AI attacks are as a result varies. However, there are some experts who expect a flood of extremely dangerous attacks in the coming years.
Below are a few concrete examples of how AI is changing cyber attacks.
Artificial intelligence improves existing attacks and makes criminals’ work easier. While phishing emails could still be easily distinguished from genuine emails with a little suspicion, some of the current phishing emails created with AI appear deceptively genuine. This means that they can hardly be distinguished from genuine emails in terms of form and content.
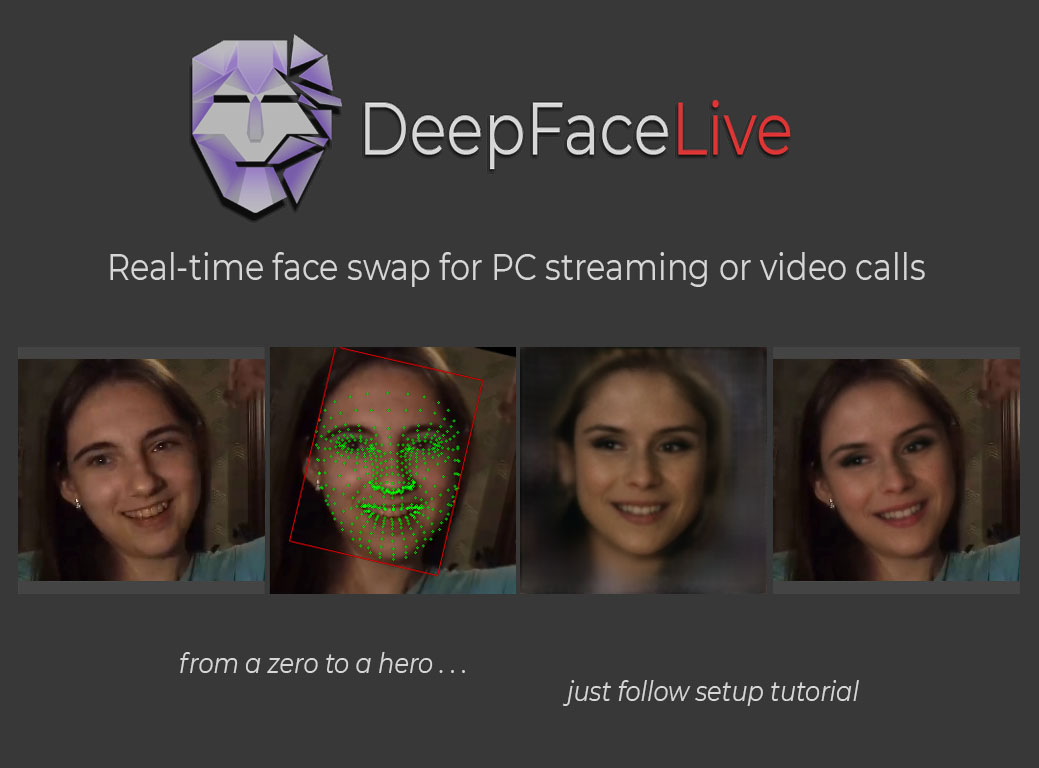
A free tool can be used to replace a face in a live video. Another tool can also be used to replace the voice.
DeepFaceLive
Internet users are also threatened by so-called deepfakes. These are, for example, videos with well-known personalities, such as a newsreader. However, this person is not reading the news on a website, but is instead advertising dubious cryptocurrencies and shares.
What’s more, attacks of this kind are much faster nowadays, as new AI tools are helping the criminals. These tools are called FraudGPT, WormGPT, AI Phish, or ScamGPT. They generate new attacks within minutes, which would otherwise have taken the criminals days.
How to protect yourself: It helps to carefully check the sender address and the links contained in improved phishing emails. You can find more information on this in our guide.
To combat deepfakes, it helps to be suspicious and take a very close look at the photo or video in question. You can find out how to recognize the scam in our guide to deepfakes.
In the following guide, on the other hand, we show you tips against attacks with fake voices.
6. Why are zero-day vulnerabilities so dangerous?
A zero-day vulnerability is a previously unknown security hole in software or an operating system for which no update is yet available. The term “zero-day” refers to the fact that the manufacturer had zero days to react to the discovered vulnerability. Either it has not yet been reported or it is already being actively exploited.
At the same time, vulnerabilities in software — at least if they are serious vulnerabilities — are a real boon for hackers. This is because they can use them to gain access to the system without having to trick the user.
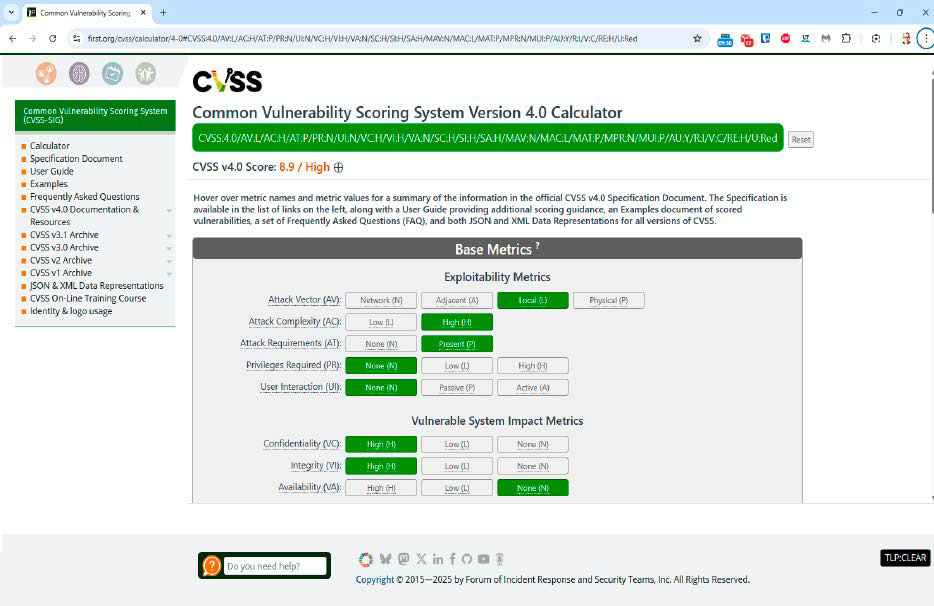
The CVSS 4.0 calculator shows how dangerous a vulnerability is according to the Common Vulnerability Scoring System, and at the same time how high the risk is that it will be exploited.
Foundry
How to protect yourself: The software itself cannot protect itself against zero-day vulnerabilities, as the corresponding update is still missing. However, the heuristics of antivirus software can usually recognize the malicious code.
In the case of high-risk zero-day vulnerabilities, however, it may also be necessary to disconnect the affected system from the internet until an update against the vulnerability is available.
7. Where can I find an online virus scanner?
In fact, there are no longer any online virus scanners that can scan your entire hard drive for malware. One of the reasons for this is that code from the browser now has significantly fewer rights on the PC than around 20 years ago, when many online virus scanners worked via ActiveX in the browser. However, today’s browsers no longer offer ActiveX support.
The term “online virus scanner” has survived, but what you get today under this name are simple antivirus programs. They are downloaded to your PC as an .exe file. Some need to be installed, others start without installation. As a second opinion to the result of your already installed antivirus program, they are certainly justified.
Examples of such virus scanners come from Eset, Trend Micro, and F-Secure.
Under the term “online virus scanner,” there are also websites where a limited number of suspicious files can be uploaded. These are then analyzed to determine whether they are dangerous.
The best-known representative of this type is VirusTotal, which scans a file with over 40 antivirus tools. The service is always worth a visit if you have a suspicious file in front of you.
8. Can I recover files encrypted by ransomware?
There are suitable decryption tools for many ransomware viruses. However, finding the right tool is usually not easy, as the ransomware virus does not disclose the code used.
You can find help on the website www.nomoreransom.org. A wizard will guide you through a process at the end of which, if all goes well, you will be offered a decryption tool for your files.
If you don’t find anything there, try ID Ransomware. If no help is offered there either, you should keep the encrypted files and check again in a few months.
Security researchers often crack the encryption codes of ransomware only after some time, or the criminals publish the master key — at least this has happened in the past.
9. How do I protect myself against ransomware?
Ideally, reliable antivirus software should recognize and block ransomware before the malware becomes active and can encrypt personal data. However, even modern protection solutions do not offer 100 percent security.
The most effective protection against ransomware is therefore an up-to-date and externally secured backup. See our roundup of the best backup software for Windows to learn more.
Windows 11 has also offered special protection against ransomware for several years.
10. Are my files safe in the cloud?
Cloud storage is not secure, but it can be made secure. There are several threats to sensitive data in the cloud: Hackers can gain access to the cloud. The cloud provider has access to the data, as do government agencies.
The cloud provider can also lock you out of your account, for example if they suspect that you have violated the rules. Something that has reportedly happened more frequently at Microsoft this year.
How to protect yourself: You can protect yourself against espionage with good end-to-end encryption. We recommend the Cryptomator tool, for example. There are apps for Android and iOS as well as tools for Windows, Linux and Mac OS. The Windows software from Cryptomator is donationware. The Android and iOS apps cost 19 euros each.
The best way to protect yourself from being locked out of a cloud account is to create a backup of your data on your own PC. This can be set up quite easily with the Cryptsync tool, for example.






